IoT Security
Internet-of-Things (IoT) basically means every device that is enhanced with Internet connectivity. While traditionally only computers, laptops, smartphones and tablets had Internet access. Nowadays, your light bulb, door ring, and even tooth brush has Internet connection and allows them to be "smart". While this smartness allows for some interesting features, the security built in (if at all) is usually not so smart. Hence, this area needs not only lots of research, but also more intense look at existing concepts and applying them to devices with maybe less energy capacity, computing power, or storage.
Secure Edge Computing
Edge Computing is an architectural paradigm in which the computation and storage of data moves closer to the sources of data, i.e., to the devices at the "edge" of the network. This paradigm is particularly useful in the context of IoT because it is not necessary to communicate all data to a central server or cloud backend. Algorithms of Artificial Intelligence can be executed on an IoT device to make decisions based on inference of the captured data. Only results or aggregated data are uploaded to the cloud, where machine learning models can be updated and then synchronized with other IoT devices.
As part of my work at Huawei, I have developed together with my colleagues a secure edge computing migration concept. Computing workloads can be migrated (together with their data) from one trusted edge computing node to another. This concept is a fundamental prerequisite to create a generic and secure fog computing architecture, i.e., combining edge and cloud computing with in-between computing nodes (the “fog”) in a flexible and trustworthy way.

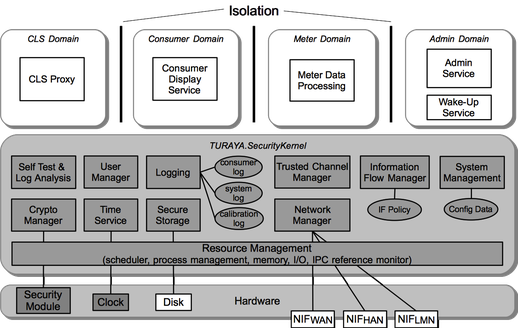
Smart Meter Gateways
As part of my work at Sirrix we developed a security architecture for smart meter gateways and leveraged earlier work on security architectures for distributed IT systems, as we did in the EMSCB and OpenTC projects, i.e., building on the Turaya security framework. Smart Meter Systems are going to be deployed worldwide. However, due to their complexity and interconnectivity, they have to deal with strict security and privacy requirements. As a result, German regulatory bodies decided a proactive approach and developed a protection profile for Common Criteria evaluation, i.e., specifying explicitly security requirements for gateway components.
The objective was to design a modular security framework that can be used to realize such gateways in order to fulfill the requirements of the protection profile. This security framework is based on a security kernel approach that has been developed within various other projects. The proposed security kernel framework offers a solution to meet these security requirements while keeping the architecture modular and flexible to be used for other implementations as well.
A key feature of the security kernel framework is that it allows executing isolated application domains on top of it. Applications belonging to one domain can communicate freely with each other. A communication to other domains is prevented by default. If communication between domains (or to external systems) should be allowed, then this must be stated in the security policy of the system.
For more information, see my presentation of the smart meter security framework.
Research Works
Edge Computing: Chancen und Sicherheitsrisiken
Marcel Winandy
M. Lang, H. Löhr (Ed.), IT-Sicherheit: Technologien und Best Practices für die Umsetzung im Unternehmen, Hanser, 2022.
Mind the Shift: Secure Migration of Containerized Processes in Edge Computing
Angelo Liguori, Peter Schoo, Marcel Winandy.
5th IEEE International Conference on Edge Computing and Scalable Cloud (IEEE EdgeCom 2019).